Security in the Cloud: It’s Complicated
When we launched the first HashiCorp State of Cloud Strategy survey earlier this year, we knew that security plays a key role in how organizations adopt cloud and multi-cloud architectures. But the survey of 3,200+ practitioners and decision makers from HashiCorp’s opt-in database revealed surprising complexity around the impact of security issues on cloud strategy.
In this blog post, we’ll take a deep dive into five key security findings from the survey. For more analysis around other aspects of the results, read this series of blog posts and check out the survey site for a visual presentation of key results and methodology.
»Security Concerns Are the Second Biggest Cloud Inhibitor
Even as cloud adoption continues to accelerate, that doesn’t mean it’s all smooth sailing. When asked about their organization’s primary cloud inhibitor, security concerns were the second most popular choice (47%), trailing only cost issues (51%). A closer look reveals some interesting differences in cloud program inhibitors by region, role, company size, and industry:
- Security was the top concern for financial services organizations and healthcare/ biotech companies. Some 59% of finserv firms named security a top-three concern, as did 52% of healthcare/biotech respondents. Notably, security was named as a top-three cloud inhibitor by just 39% of entertainment/media firms and 41% of software and services companies.
- Geographically, security concerns were most pervasive in the Asia-Pacific region, cited by 52% of respondents, while respondents in Europe/Middle East/Africa had the lowest percentage (39%).
- Security concerns also varied significantly by organization size. Not surprisingly, perhaps, small businesses (<100 employees) were least concerned, with just 38% of these respondents calling security a top-3three cloud inhibitor, compared to 55% of large enterprises (>5,000 employees).
- By role, business decision makers (40%) named security as a top-three cloud inhibitor notably less often than practitioners (47%) and technical decision makers (46%) did.
Why might business decision makers see security as less of an inhibitor than do practitioners or technical decision makers? Possibly because business decision makers must weigh the costs and benefits of moving to the cloud, whereas practitioners and technical decision makers are tasked with implementation and focus more on how to make it successful.
»Security Can Also be a Multi-Cloud Driver
But just as cost calculations in the cloud can be complicated, security isn’t just a cloud concern for the survey respondents, it can also be a cloud benefit.
When asked what business and technology factors were driving their multi-cloud adoption, security and governance was mentioned in the top three by 16% of respondents. As you might expect, cloud security was an even more important driver in the public sector (19%) and the financial industry (18%). One significant geographical difference was that only 11% of Latin American respondents cited security as a multi-cloud driver.
Security doesn’t live in isolation. According to one solution engineer, “The main thing is the security concerns, privacy, regulatory control of the data, and all costs involved around it.” But as another security engineer noted, “Cloud services allow more granular security controls.”
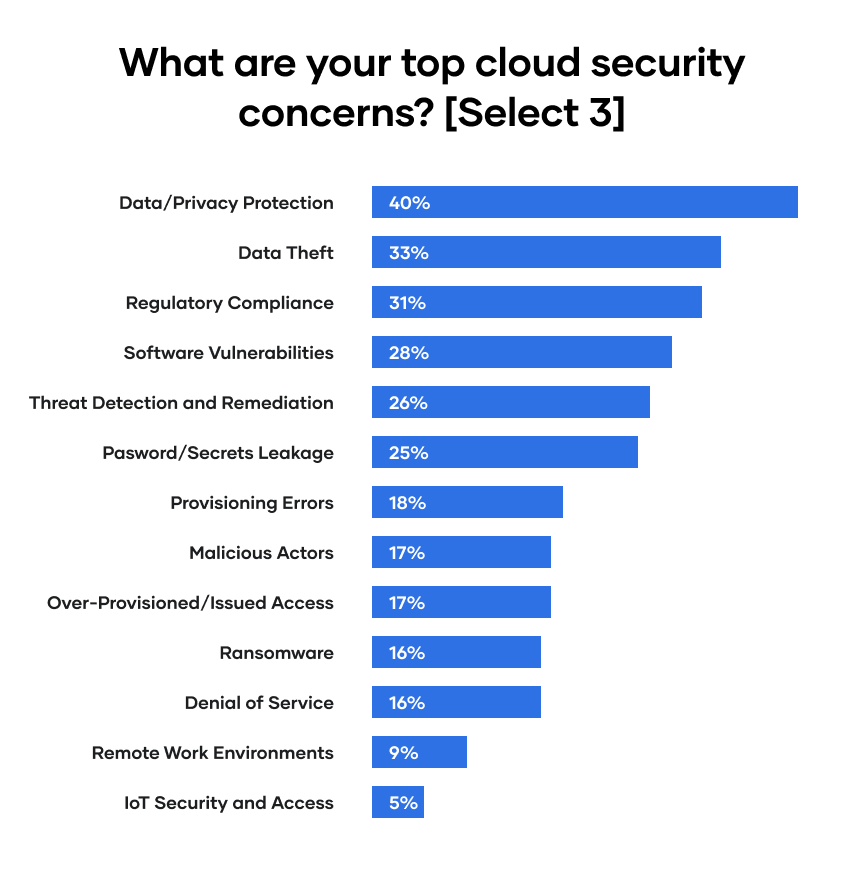
»Data/Privacy Protection Is the Top Cloud Security Concern
The concept of security can cover many things, so what exactly are practitioners and decision makers really worried about? A lot of different things, it turns out, and no single concern was mentioned by more than half of respondents.

»Skills Shortages Affect Cloud Security, Too
If those are the security threats, what’s keeping organizations from solving them? When it comes to security, the most common challenges involve staff and skilling issues, cited by more than a quarter (26%) of respondents.

Notably, a shortage of the proper skills was called out as a top-three challenge to operationalizing multi-cloud overall by more than half (57%) of respondents. That could be why almost 18% of respondents are using or plan to use commercial security tools as a service. Interestingly, only 3% of respondents were concerned about financial costs when it comes to security, possibly because security is considered so important that when a security issue is identified, a budget will be allocated to address it.
»Security Automation Tools Are Becoming More Essential
Survey respondents overwhelmingly agreed that the right tools are critical for managing multi-cloud environments and for every component of their cloud efforts, including provisioning, networking, security, and application deployment. Ninety-four percent of respondents called infrastructure automation tools “important” or “extremely important” to operationalize their multi-cloud environments.
Surprisingly, despite the importance of security in cloud environments, just about half (50%) of respondents use infrastructure automation tools in the security arena, trailing provisioning (75%), application deployment (69%), and networking (58%). That may be about to change, however, as 44% of respondents plan to use infrastructure automation tools for security, easily topping the other four components.

»Conclusion
Survey respondents from different industries expressed varied cloud inhibitors, security concerns, business challenges, and provided insight into cloud adoption. Not too surprisingly, a current area of focus across industries is a shortage of the skills needed to help implement their cloud initiatives. As noted above, that could be why so many companies are looking to leverage security automation tools.
For more insights into how companies are transitioning to the cloud and multi-cloud environments, check out the full HashiCorp State of Cloud Strategy Survey. And read more survey analysis in the HashiCorp blog.
Source: HashiCorp Blog